Securing the copyright marketplace have to be built a precedence if we need to mitigate the illicit funding from the DPRK?�s weapons packages.
Numerous argue that regulation effective for securing banks is significantly less effective from the copyright space due to sector?�s decentralized mother nature. copyright wants extra safety rules, but In addition, it requirements new methods that bear in mind its distinctions from fiat economic establishments.,??cybersecurity measures could develop into an afterthought, specially when businesses absence the cash or personnel for these types of actions. The challenge isn?�t one of a kind to People new to company; on the other hand, even properly-recognized businesses may well Allow cybersecurity drop to your wayside or may absence the education and learning to grasp the promptly evolving threat landscape.
Policy remedies ought to place more emphasis on educating marketplace actors about important threats in copyright as well as purpose of cybersecurity even though also incentivizing larger security standards.
Plainly, This really is an unbelievably profitable enterprise with the DPRK. In 2024, a senior Biden administration official voiced problems that about 50% with the DPRK?�s overseas-forex earnings came from cybercrime, which includes its copyright theft functions, as well as a UN report also shared statements from member states the DPRK?�s weapons method is largely funded by its cyber operations.
On the other hand, issues get difficult when one particular considers that in The usa and many nations around the world, copyright continues to be largely unregulated, and the efficacy of its current regulation is often debated.
These threat actors were then ready to steal AWS session tokens, the non permanent keys that enable website you to request momentary credentials on your employer?�s AWS account. By hijacking active tokens, the attackers ended up in a position to bypass MFA controls and attain entry to Harmless Wallet ?�s AWS account. By timing their efforts to coincide Along with the developer?�s typical work hours, Additionally they remained undetected right until the actual heist.
 Scott Baio Then & Now!
Scott Baio Then & Now! Andrew Keegan Then & Now!
Andrew Keegan Then & Now! Heath Ledger Then & Now!
Heath Ledger Then & Now!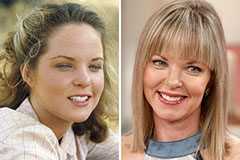 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now! Lacey Chabert Then & Now!
Lacey Chabert Then & Now!